Fig. 1
From: Detecting command injection attacks in web applications based on novel deep learning methods
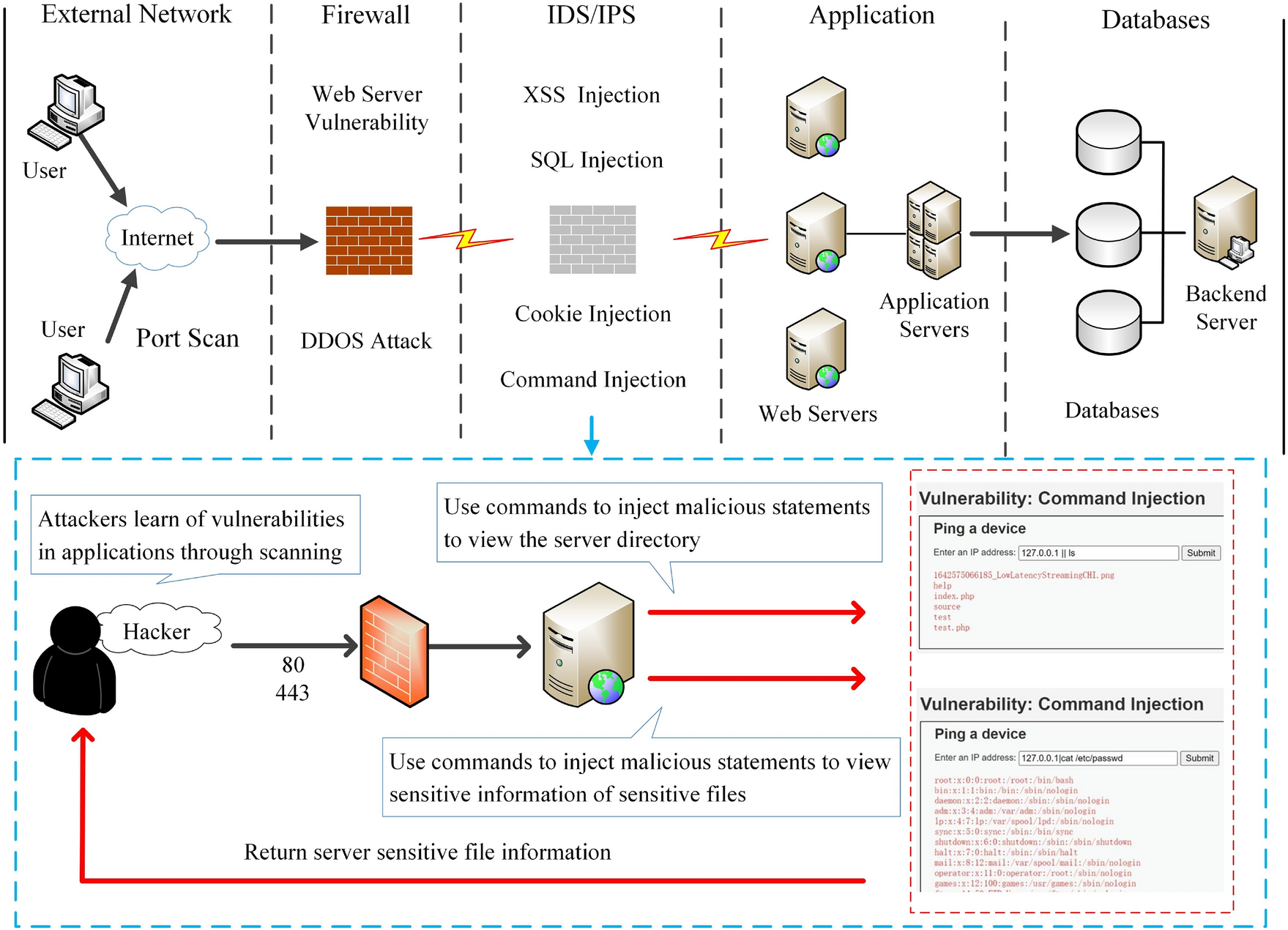
Web command injection attack topology.
From: Detecting command injection attacks in web applications based on novel deep learning methods

Web command injection attack topology.